PlonK Deconstructed 8: Round 3
Ben Bencik
Round 3
We have introduced the permutation polynomial which should guarantee that copy constraints are satisfied. By construction of the quotient polynomial the prover will show that the permutaiotn polynomial is valid and the gate constraints hold. But first, we will introduce a check to verify that some polynomial is zero over a specified domain.
Round overview:
Compute quotient challenge
Compute quotient polynomial
Split into polynomials of smaller degree
Compute and blind polynomial parts
Commit and output , ,
Zero test
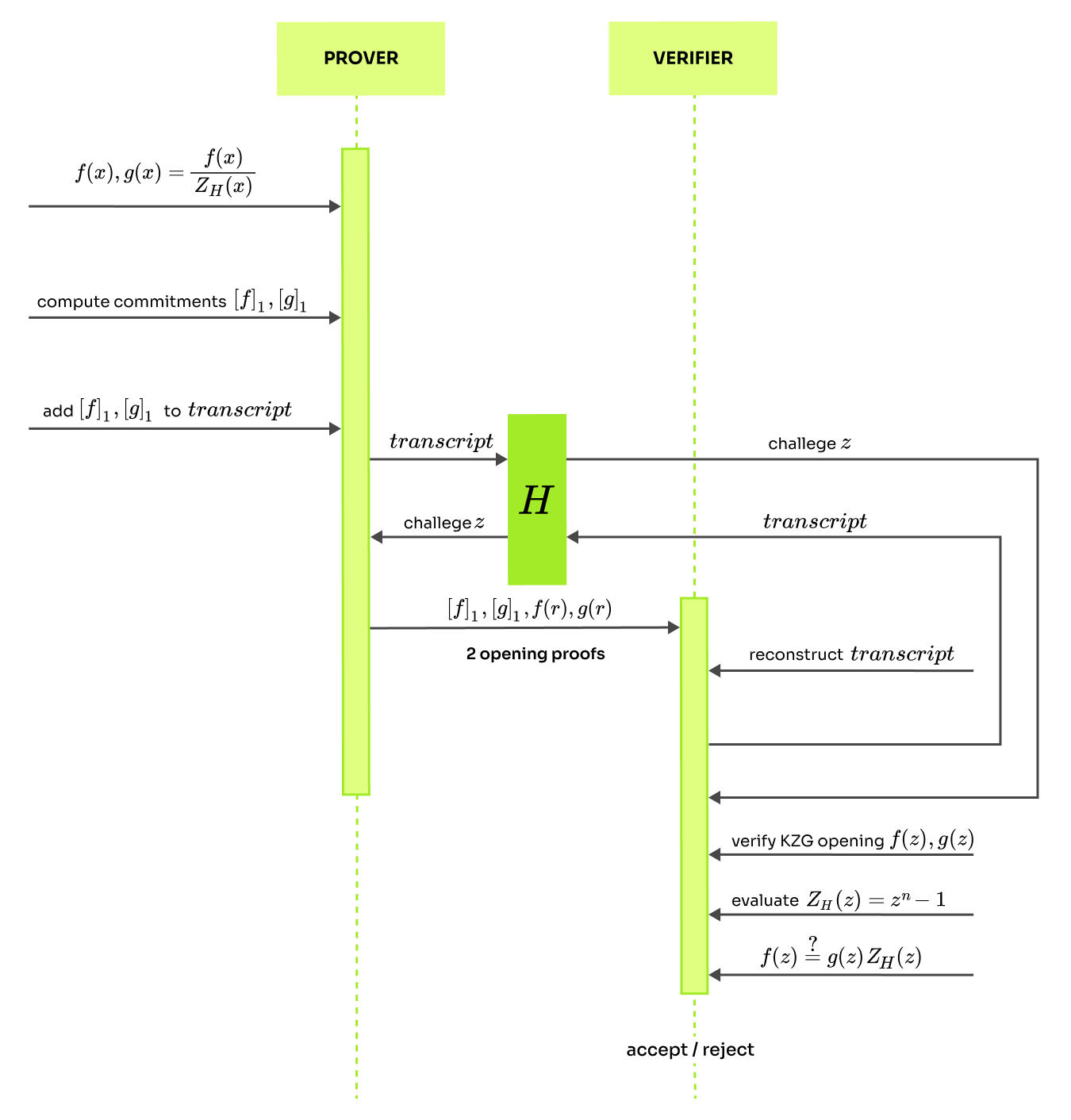
In this round, we will need to prove that some polynomials evaluate to 0 over the whole domain . Luckily, we have all the tools that we need. If some polynomial is zero on , then every element of has to be a root, which means it can be factored as where is the vanishing polynomial. This implies that a polynomial is zero on if and only if it is divisible by . The observation enables to change the zero check into a divisibility check. To verify that , the verifier checks evaluation at a random point as . The security of this check was discussed in the preliminaries. To make sure that are evaluations of we will use the KZG polynomial commitment scheme.
This check is sound (does not pass if is not zero on ), because if the polynomial is not zero on the whole domain , then it cannot be divided by . As result, the prover cannot provide that would satisfy . To put this into context, this test can be made into a standalone, non-interactive protocol that uses the KZG polynomial commitment scheme. Below is a detailed diagram of how it works. We use a random oracle to generate the challenge based on a transcript.
Checking permutation polynomial
In the previous round, we computed and committed to the permutation polynomial . However, we did not prove that it was computed correctly. Specifically we have promised that , otherwise it is cumulative product . This is equivalent to checking:
where are:
Why are the above checks sufficient? (optional section)
1. work?
- if then evaluates to 1 and we are left with which is 0 only if effectively checking what we wanted
- if the Lagrange basis evaluates to 0 and we get
2. check?
The second statement checks if the permutation polynomial was computed as a cumulative product . The claim is that if then the polynomial was computed as specified by the protocol. We can prove this claim inductively by showing that it holds for supposing it holds for :
The functions are similar to the from the previous round. But why do we perform the check with instead of ? The functions are computed in evaluation form from the values of and while are computed from interpolations of and . This means that and agree on the evaluation domain .
The permutation polynomial was calculated in the evaluation form and consequently interpolated. To check that the prover used correct values for the witness , the verifier can check the permutation polynomial against , which interpolate . The important thing is that the commitments were calculated before the permutation polynomial, so the prover is bounded to the witness before he starts constructing the permutation polynomial.
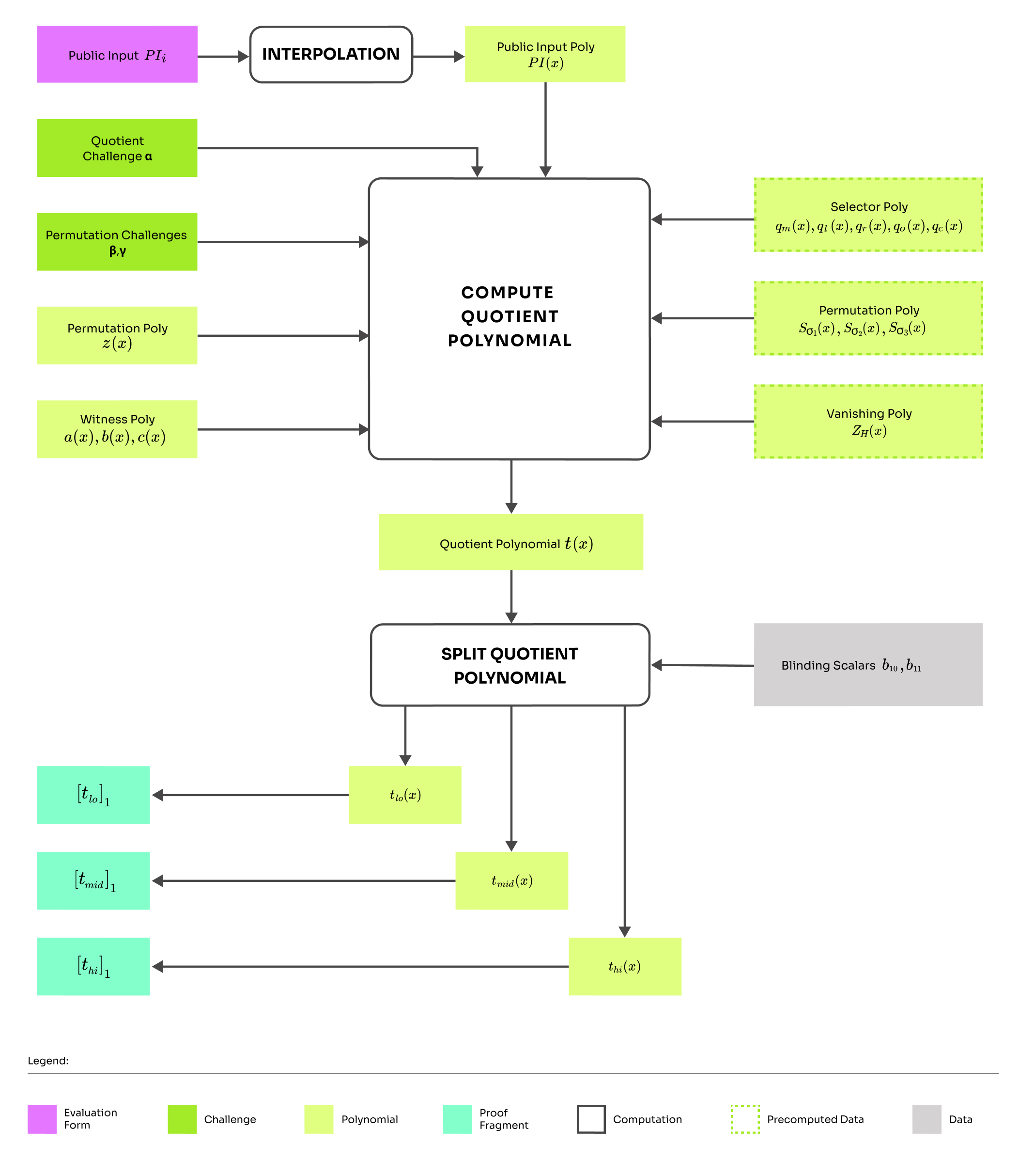
Computing quotient polynomial
The quotient polynomial might look complicated at first sight, but it is only an aggregation of the arithmetic gate check and the permutation copy constraint check. We will split it into such that .
The first term might feel familiar. This is the gate constraint introduced in the arithmetization. This term ensures that each gate is evaluated correctly. To be more specific, if it evaluates to zero at that means the gate is computed correctly.
The term corresponds to the 2. check from the previous section. The check was introduced as: . But after rearranging we get
Finally, the last term is the 1. check from the previous section checking .
One common thing for each term is the division by the vanishing polynomial and multiplication by some . The division by application of the zero test described above. The multiplication by ensures that the quotient polynomial evaluates to zero only if all of the separate terms evaluate to zero.
Why do we multiply by ? (optional section)
We might get an unsound protocol if we compute the quotient polynomial without multiplication by a random . For example when then the quotient polynomial evaluates to 0 even though are not valid. The prover might want to use this to cheat the protocol. We can prevent it by multiplying the terms with a random linear combination which is a standard technique for batching checks in cryptography.
The important thing is that the commitments to polynomials are part of the transcript, which affect the choice of the challenge. Since, it is not possible to discover the challenge before the commitments it is hard to cheat the protocol as in the example above.
If then naturally . However, if some of the terms is non-zero, there is only a negligible probability that after multiplication by a random linear combination will be 0.
Splitting quotient polynomial
Amazing, now we know how to construct the quotient polynomial. However, the resulting polynomial degree is too big. We want our polynomials to have the maximum degree of . Why? We assumed so in the setup while creating SRS. However, it is possible to split into smaller polynomials of degree degree and of degree at most such that:
Why is the degree of the quotient polynomial ? (optional section)
The degree of is determined by where we multiply wire polynomials and permutation polynomial . Each of the wire polynomials has degree bound , and the permutation polynomial has , which makes it , but is also divided by of degree . Therefore, the degree bound of the quotient polynomial is .
The quotient polynomial has a degree at most , which means it can be written as . Then we can split as:
This looks better, but we forgot something. Before committing, we want to blind the polynomial so that the protocol remains zero-knowledge. Here the prover chooses two random blinding scalars and blinds the polynomial as: . Finally, we calculate the commitments , , and move to the next round, where we will calculate polynomial openings and show a neat trick to minimize the number of openings.
List of the PlonK blog posts:
- 1: Overview
- 2: Arithmetization
- 3: Math Preliminaries
- 4: KZG
- 5: Setup
- 6: Round 1
- 7: Round 2
- 8: Round 3
- 9: Round 4
- 10: Round 5
- 11: Verification
If you have any suggestions or improvements to this blog, send an e-mail to contact@maya-zk.com