PlonK Deconstructed 7: Round 2
Ben Bencik
Round 2
In this post, we will talk about the copy constraints that ensure the "circuit is wired correctly". We will describe how to handle the copy constraints and build the permutation polynomial from the ground up.
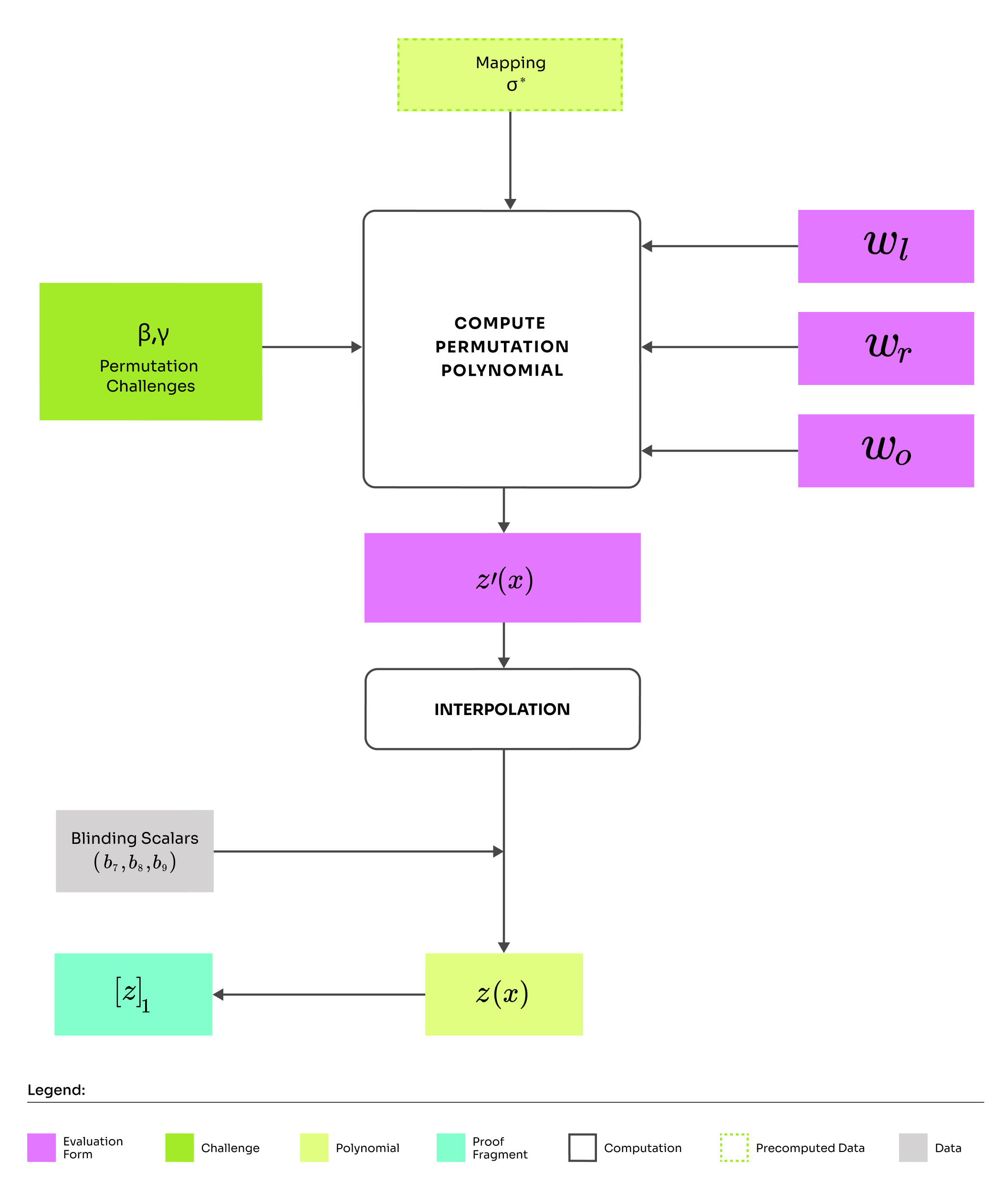
Round overview:
Receive permutation challenges
Compute permutation polynomial
Compute and output commitment
Permutations
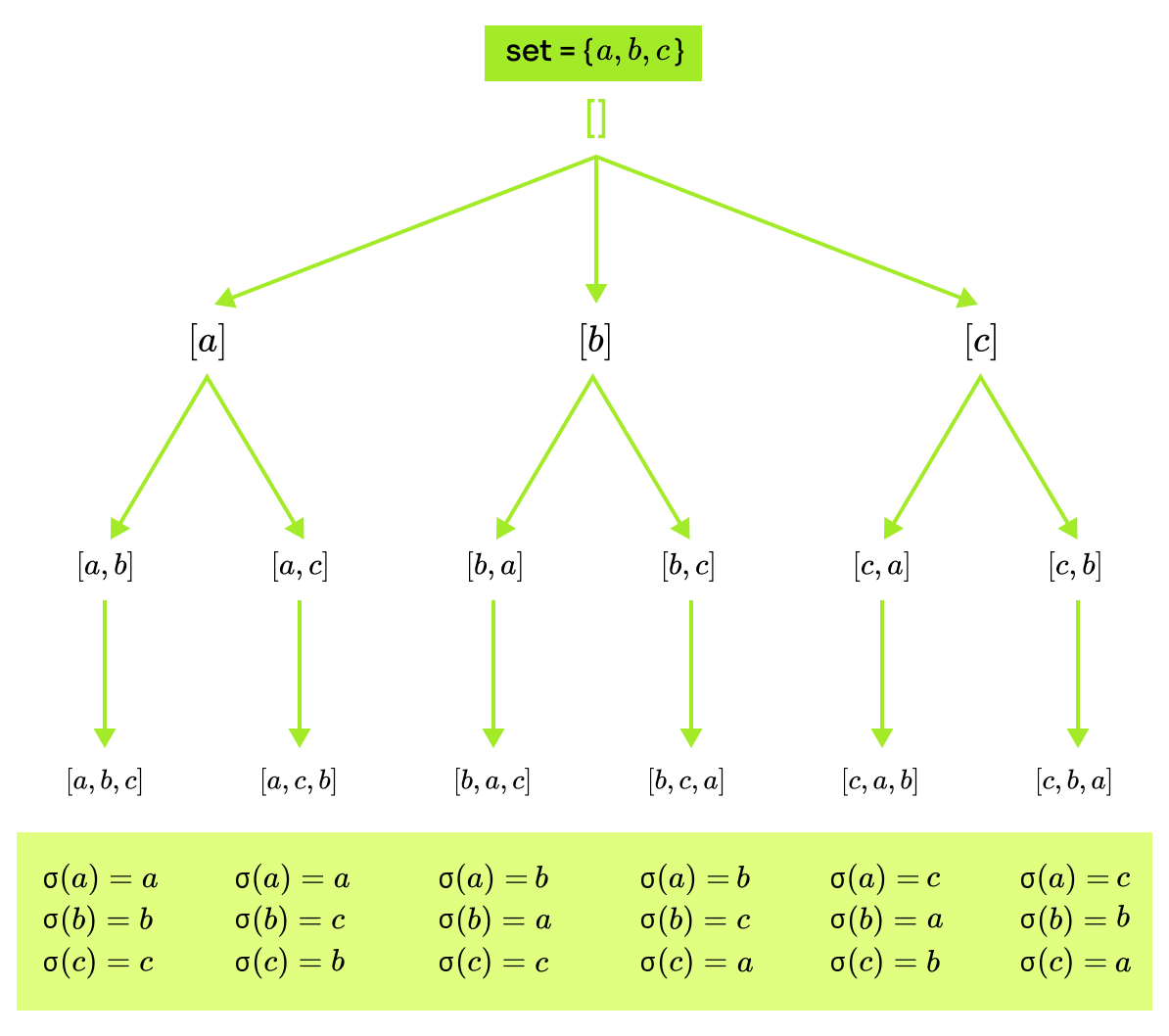
To start from the very basics, a permutation is an ordering of a set. Take a set of elements then is a permutation, and so is but not . A permutation is mapping that express some shuffling. Below are expressed all permutations for .
Why is this useful? If you look back at the computation table from arithmetization, it is clear that some cells must be equal. Each gate represents some computation, and the edges of the graph or "wires" define the flow of the variables. By connecting to , we express that the output of is passed as input to . It should hold output of input to . How can the prover convince the verifier that these constrints are satisfied?
Put the variables into boxes such that in each box, all variables have the same value. We can say that we create equivalence classes, depending on how the gates are wired. In each box, the variables are somehow ordered. We will want to construct a permutation function that changes the order of the elements in each box. The function is usually implemented as a rotation of the elements in the equivalence classes.
Consider witness vector which has size and is composed of such that . This is how the permutation would look for the example diagram from arithmetization.
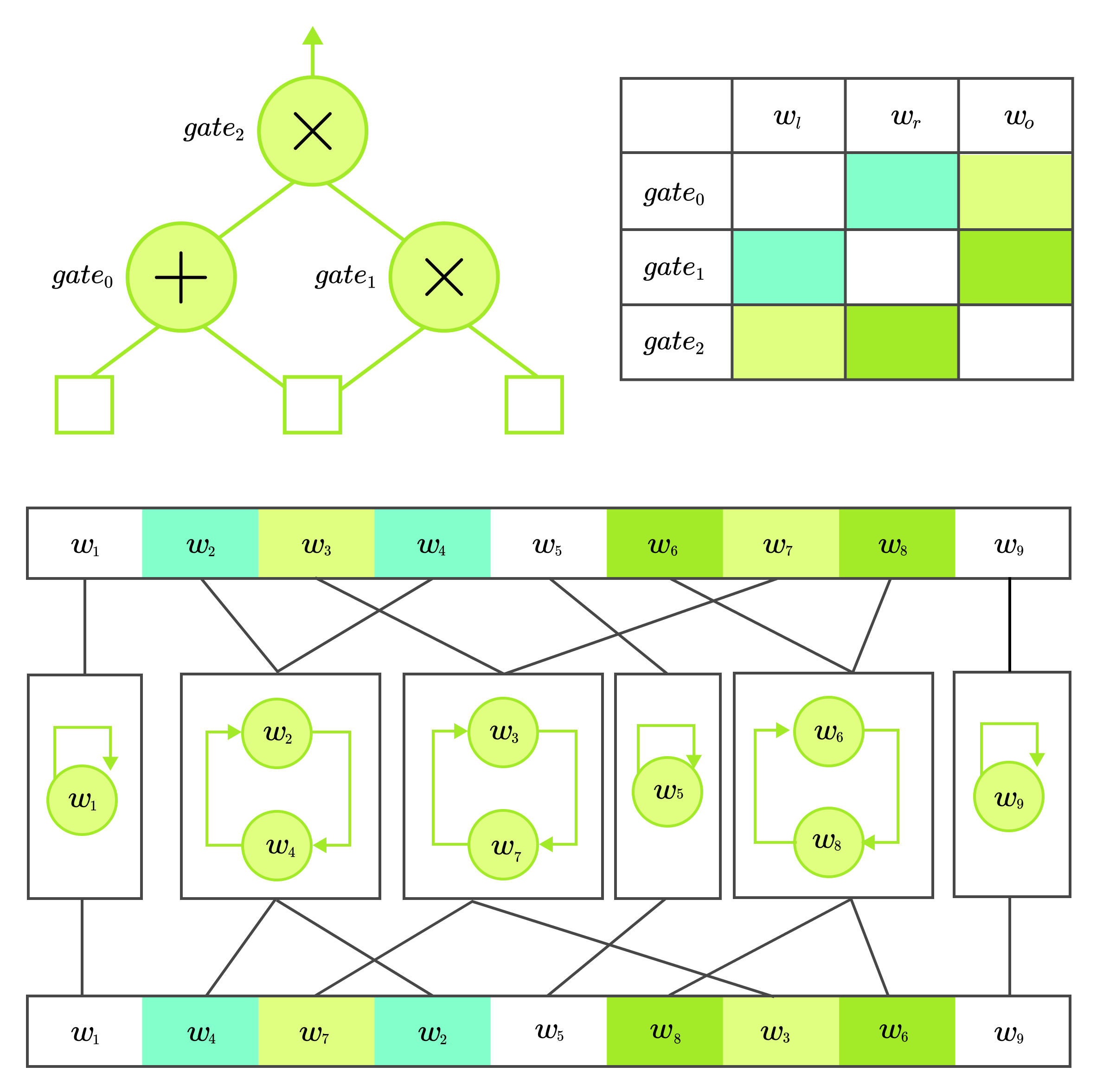
No matter on the input of the circuit the values in the equivalence class must always contain the same value. This specific circuit thus has copy constraints
We can prove that the copy constraints hold by showing that holds for every index . Say there is constraint and we get:
Naturally, the expressions above are satisfied if and only if . That is the core idea that will be used in the permutation check. Now, we would like to effectively use this observation in the protocol.
In the following section, we will build the permutation polynomial from the ground up. We will first show how to check that two vectors are permutations of each other. Then, we will try to detect a specific permutation on a vector. And finally, we will see how to check permutations across multiple vectors.
Permutation check
An enemy gives you two vectors , and you need to quickly decide if they are permutations of each other. You could naively compare the elements one by one, but that is too slow. Instead you can try to aggregate the vectors into a single value and perform, something like a product check:
This approach satisfies correctness, because multiplication is commutative. However it does not satisfy soundness, meaning the check can pass even if the vectors are not equal. For example, vectors and would pass the check, but they are not permutations of each other. What if the sample an element and perform a variation of the product check:
This check is also correct because of the commutativity of multiplication, but what about the soundness? The whole trick is to think of this expression in terms of polynomials where each side of the equation is a polynomial evaluated at a randomly selected point . From the previous post we know that that if this check succeeds, then the polynomials are equal with very high probability.
Intra-vector check
This is really nice, but the problem is that no specific permutation is enforced. How can we enforce a permutation that is defined as rotation on the equivalence classes? We have two vectors and a permutation . The trick is to encode the elements as where for the index, we will use the elements of evaluation domain . Below is an example where the permutation swaps the last two elements.
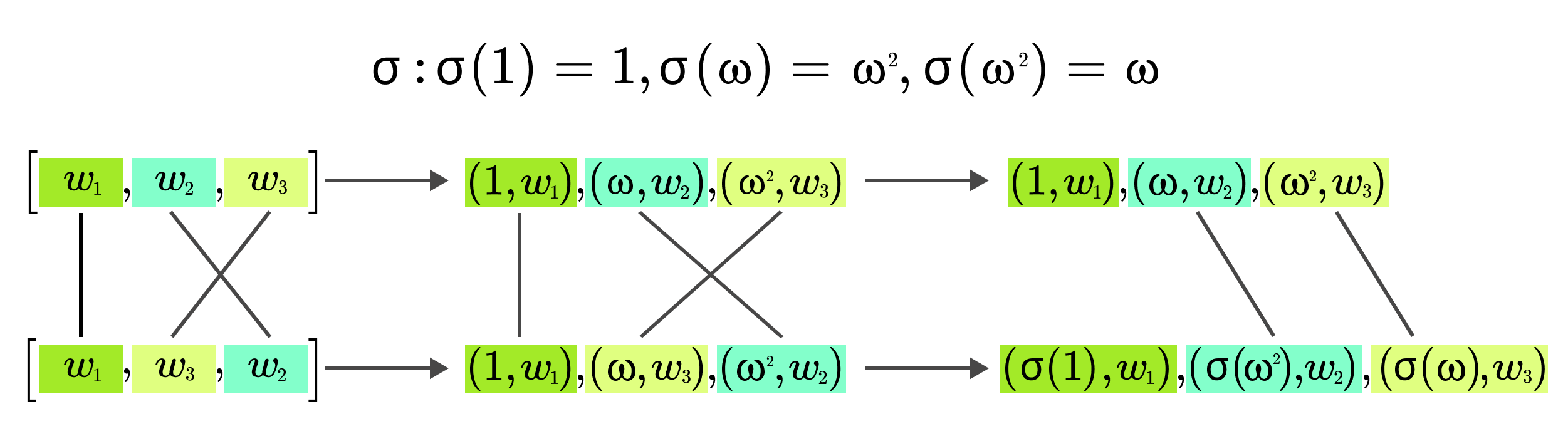
Okay, but the permutation check above relies on the fact that we were comparing polynomials, so we somehow need to write the tuples as polynomials. We will construct a random linear combination, therefore becomes where is randomly sampled.
Why can we use this encoding of tuples? (optional section)
In order to use this check safely in the protocol, we need to be sure that
The answer is polynomials. Notice that is a linear polynomial with coefficients evaluated at , and so is just with different coefficients. We know that comparing polynomials at a randomly selected point gives us a good guarantee that the polynomials are equal. So we conclude that if the random linear combinations are equal, then with very high probability also, the tuples are equal.
Now we can put everything together. We will use the permutation check and enforce specific permutation by encoding tuples as random linear combinations. This finalizes the check for a specific permutation on a single vector.
To sum it up, we have shown that the copy constraints of the arithmetic circuit could be represented as a permutation. First we tried to perform effective check of arbitrary permutation and then check for a specific permutation. Once again, the answer lay in converting everything to polynomials. The last obstacle in constructing the permutation polynomial is that we need to be able to check permutation across multiple vectors.
Inter-vector check
In this case, we will want to check the permutation across vectors , which are columns of the computation table described in arithmetization. Each of has size and we will concatenate them into which has size . The domain is no longer sufficient for indexing because it has size . We will solve this by using larger , where are chosen such that all elements in are distinct.
Here we will use the from setup. It also performs rotation on the equivalence classes, we just need to extend the domain and image to accommodate values. Using the same ideas as before, we construct the check for the inter-vector case.
q(i) = (w*{i} + \beta \sigma^_ (i) + \gamma)(w_{n+i} + \beta \sigma^_ (n+i) + \gamma)(w_{2n+i} + \beta \sigma^* (2n+i) + \gamma)
This expression might be undefined when is 0. However, this only happens with negligible probability. When it happens, the protocol is instructed to abort and repeat with other randomly sampled .
The Permutation Polynomial
How can we convince the verifier that this check succeeds? We cannot give him the values to compute the check, because he would discover , which violates zero-knowledge. Moreover the verifier should run in time smaller than , so this computation would be too heavy. Unsurprisingly, we will solve this problem by constructing the permutation polynomial, which is defined as:
The essential idea of the permutation check remains the same. We are taking the product of ratios, where the numerator represents the former set and the denominator represents the permuted set. If each of these ratios is 1 that means the copy constraints are satisfied. How do we construct this polynomial? We will proceed as usual and interpolate the values over the domain .
To enforce that the permutation polynomial evaluates to 1 on we add the Lagrange basis . To finish it up, we add blinding. This time, we will need a blinding polynomial of degree 2 because the permutation polynomial will be used in two proofs of polynomial openings () in round 5.
Great, and that is all there is to the permutation polynomial. The prover can happily finish round 2 by committing to the permutation polynomial. In the next post about round 3, we will show how to construct the quotient polynomial and prove that the permutation polynomial was computed correctly.
List of the PlonK blog posts:
- 1: Overview
- 2: Arithmetization
- 3: Math Preliminaries
- 4: KZG
- 5: Setup
- 6: Round 1
- 7: Round 2
- 8: Round 3
- 9: Round 4
- 10: Round 5
- 11: Verification
If you have any suggestions or improvements to this blog, send an e-mail to contact@maya-zk.com